What is a botnet?
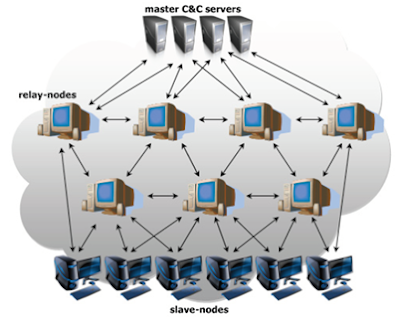
A botnet, which is short for robot network, is a group of computers that have been taken over and controlled remotely. Known as zombie computers or bots, these computers for the most part operate like a normal computer, leaving owners unaware that their machine is infected. They typically receive instructions from a central PC that is known as the command-and-control centre. A botnet is usually made up of tens or hundreds of thousands of home computers.
Bots were originally designed to help transmit spam. Since their creation, they have been modified to engage in illegal activities as well.
Botnets are commonly used for:
■ DDoS (distributed denial of service) attacks
DDoS attacks attempt to overload a site in order to disrupt business by creating a loss of connectivity or connection bandwidth.
■ Click-fraud
Certain advertising firms pay website hosts a small fee every time an ad of theirs is clicked on. Some botnets take advantage of this by having computers access the site repeatedly in order to fraudulently obtain payment from the advertiser.
■ Phishing campaigns
These are used to harvest email addresses. Zombies within a botnet are used to send out spam and phishing email in order to collect addresses to add to their spamming lists.
■ Keylogging
Software is installed that records keyboard activity that is send back to the botnet. Keylogging programs to try to gain your personal information, such as usernames, passwords and credit cards.
■ Host malicious web sites
Botnets can use home computers to create malicious websites that download malware when accessed.
Some botnets can also install malicious software that causes infected computers to infect other computers. Since these botnets get their instructions from other hacked computers it can be hard to trace which computer is the command-and-control centre.
How does your computer become a bot?
Home computers that have security vulnerabilities are prime targets for botnets. Spammers scan the Internet looking for computers that are unprotected and use these “open-doors” to install malicious software. Another tactic is through phishing or spam emails that contain links or attachments. When clicked-on or opened, malware is then installed on the machine. Furthermore, visiting certain websites can result in malicious software being installed. This malicious software may cause your computer to run slower, your ISP (Internet Service Provider) to shut down your account for spamming, or you becoming a victim of identity theft.
Warning signs
Your computer may be part of a botnet if:
■ Your computer suddenly starts operating slowly or erratically
■ You receive emails accusing you of sending spam
■ You have email messages in your outbox that you didn’t send
How to protect yourself
To prevent your computer from becoming infected:
■Use up-to-date anti-virus and anti-spyware software
Look for software that removes viruses and updates itself automatically on a daily basis. Be wary of ads on the Internet offering spyware software, as this might be a ploy to get you to download malicious code.
■Set your operating system software to download and install security patches automatically
These security patches released monthly by Microsoft help fix any flaws companies find in their operating system which in turn helps to give your computer the latest protection.
■Insure that your firewall is turned on
Firewalls are designed to prevent hackers from accessing your computer by making you invisible on the Internet. They help to block incoming communications from unauthorized sources. Many operating systems like Windows and Mac OS X have built-in firewalls however you may need to check to see if it is enabled. Routers have hardware firewalls. It is especially important to have your firewall enabled if you have a broadband connection because the connection is always open. For more information see http://www.ucalgary.ca/it/security/firew…
■Be cautious about opening any attachments, or downloading any files from emails you receive
Even if the email is from a friend or co-worker, be careful about what you choose to open since their computer could be compromised. If you send an email attachment, explain in the email what the attachment is.
■Be careful what you download from the Web
Only visit sites you trust. It is recommended that you use a web browser that has security features or use a program like SiteAdvisor that checks the status of websites to insure that they are safe to visit and use.
■Turn off your computer when you aren’t using it
If you’re disconnected from the Internet, hackers can’t get to you.
RAC 007
No comments:
Post a Comment
Please write your comments here on the above post(s).